
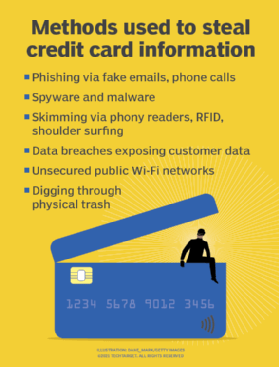
Here's How Much Your Personal Information Is Worth To Cybercriminals – And What They Do With It - Texas A&M Today

Hackers steal information. Hacker stealing money and personal information. Hacker unlock information, steal and crime computer data. Vector illustration. Stock Vector | Adobe Stock

Is Your Stolen Data Being Sold on the Dark Web? | Cloud-Based Business Communications & Networking: UCaaS, CCaaS, SD-WAN

















![Hackers steal information. Hacker stealing... - Stock Illustration [68174836] - PIXTA Hackers steal information. Hacker stealing... - Stock Illustration [68174836] - PIXTA](https://en.pimg.jp/068/174/836/1/68174836.jpg)

